
JOB PROGRAM
Cybersecurity Job Program
Transition to Cybersecurity Specialist role in just 24 weeks — with assured 5 job interviews!!
Transition to Cybersecurity Specialist role
in just 24 weeks — with assured 5 job interviews!!

100% Moneyback Guarantee
Reserve your spot today!
Basic Info
Select Offers
Application closes on:28 Jan 2026
Get instant access of pre-course material!
Talk to Us
We’re here to help! Reach us at:
What is in it for you?
Shape the future with Cybersecurity Specialist Job Program
 Live Classes
Live Classes
 Instructor-led Live Sessions
Instructor-led Live Sessions
Attend 4 weeks of instructor led live classes from top 1% industry experts
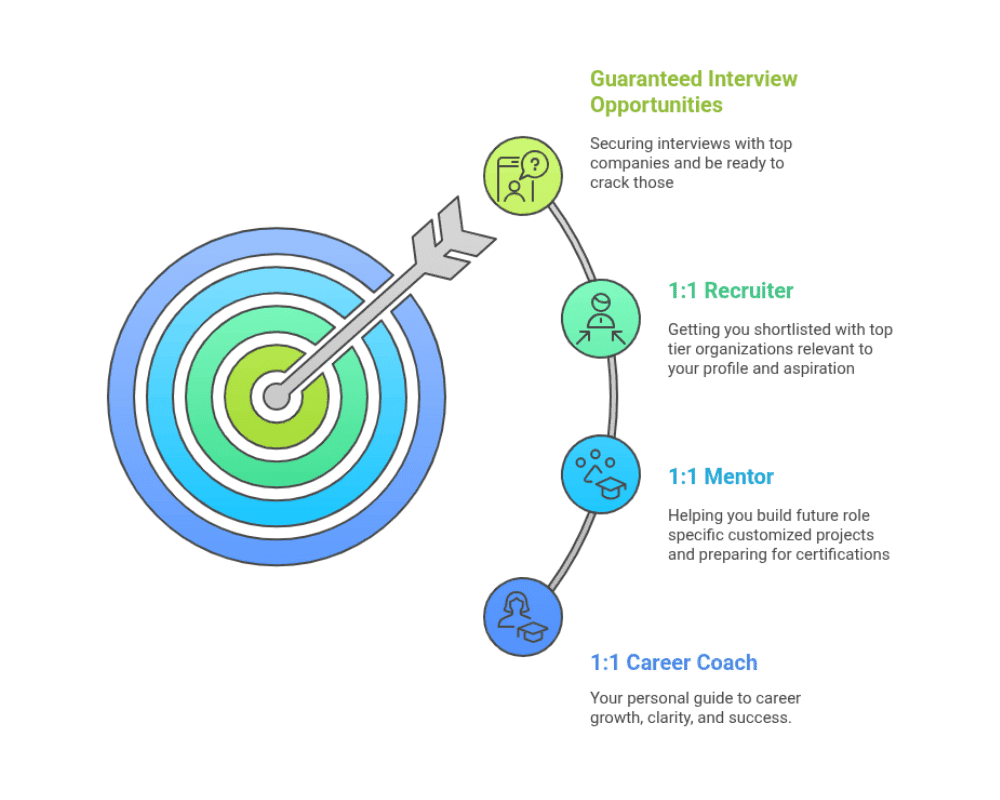
1:1 Career Coach
1:1 Career Coach for Profile Building
Get personalized career guidance and actionable steps to achieve your career goals with a dedicated career coach.
1:1 Mentor
1:1 Mentor for 2 Projects
Get personalized 1:1 guidance & hands-on support on projects and certifications to build your career.
1:1 Recruiter
1:1 Recruiter for 5 Job Interviews
Dedicated recruiter to identify job opportunities and get you shortlisted for 5 top companies in your domain.
Flexible Schedule
Flexible Schedule
Choose live classes from different cohorts that fit your availability and get access to 24/7 support.
International Job Opportunities
International Job Opportunities
Get access to international job opportunities and get hired by top companies across the globe.
Grab your spot before it’s gone
Discount applicable for next 3 candidates
100% Moneyback Guarantee
Talk to Us
We’re here to help! Reach us at:
WhatsApp calls are also available on both numbers.
Grab your slot before the offer expires
Discount applicable for next 3 candidates only.
Reserve your spot today!
Basic Info
Select Offers
Application closes on:28 Jan 2026
Get instant access of pre-course material!
Talk to Us
We’re here to help! Reach us at:
Learn from Top 1%
Sr. Managers, VPs, CXOs, Directors & Founders from companies shaping the future.

Guaranteed 5 Interviews with Top Companies
Unlock assured interview opportunities with top companies through our recruiter network, supported by 1:1 recruiters, mentors, and career coaches to guide you toward success.
Payment Offers
Reserve your spot today!
Top 1% Recruiters - Get interview access to 550+ Companies

Career Pathway
Curriculum
A Curriculum designed for your success
Live Sessions Schedule ![]() Sat - Sun (Weekends Only)
Sat - Sun (Weekends Only) ![]() Timing 7:00 AM - 9:00 AM / 8:30 AM - 10:30 AM / 11:00 AM - 1:00 PM / 5:00 PM - 7:00 PM / 7:30 PM - 9:30 PM EST
Timing 7:00 AM - 9:00 AM / 8:30 AM - 10:30 AM / 11:00 AM - 1:00 PM / 5:00 PM - 7:00 PM / 7:30 PM - 9:30 PM EST
- Introduction to Ethical Hacking
- Information Security Overview
- Information Security Threats and Attack Vectors
- Ethical Hacking Concepts
- Information Security Controls
- Penetration Testing Concepts
- Information Security Laws and Standards
- Footprinting and Reconnaissance
- Footprinting through Search Engines, Web Services, and Social Networking Sites
- Website Footprinting
- Email Footprinting
- Competitive Intelligence
- Whois, DNS, and Network Footprinting
- Footprinting through Social Engineering
- Footprinting Tools
- Countermeasures
- Footprinting Pen Testing
Job Program Includes

1:1 Career Coach

1:1 Project & Certification Mentor

1:1 Recruiter

1:1 Profile Building

LIVE Interactive Sessions

Quizzes, Assignments & Projects

Study Materials & Session Recordings

Verified Certificate
Instructors

Ankesh P
15+ Years, Cybersecurity Manager, Deloitte

Vibhuti S
13+ Years, CyberSecurity Sr. Manager, PayTm
Job Program Includes

1:1 Career Coach

1:1 Project & Certification Mentor

1:1 Recruiter

1:1 Profile Building

LIVE Interactive Sessions

Quizzes, Assignments & Projects

Study Materials & Session Recordings

Verified Certificate
Course Pre-requisites
.ffb97545.png&w=16&q=75&dpl=dpl_6TSu5AqX4Gsythkwbfan4SsZGFHu) Handling software knowledge is required for this course.
Handling software knowledge is required for this course.
Designation & Career Path
.ffb97545.png&w=16&q=75&dpl=dpl_6TSu5AqX4Gsythkwbfan4SsZGFHu) Cybersecurity Analyst – Monitor systems, detect vulnerabilities, and respond to security incidents to protect organizational assets.
Cybersecurity Analyst – Monitor systems, detect vulnerabilities, and respond to security incidents to protect organizational assets..ffb97545.png&w=16&q=75&dpl=dpl_6TSu5AqX4Gsythkwbfan4SsZGFHu) SOC Analyst – Investigate alerts, analyze logs in Splunk SIEM, and coordinate incident response within a Security Operations Center.
SOC Analyst – Investigate alerts, analyze logs in Splunk SIEM, and coordinate incident response within a Security Operations Center..ffb97545.png&w=16&q=75&dpl=dpl_6TSu5AqX4Gsythkwbfan4SsZGFHu) Cloud Security Engineer – Implement and manage security controls for AWS and Microsoft cloud environments, ensuring compliance and data protection.
Cloud Security Engineer – Implement and manage security controls for AWS and Microsoft cloud environments, ensuring compliance and data protection..ffb97545.png&w=16&q=75&dpl=dpl_6TSu5AqX4Gsythkwbfan4SsZGFHu) Information Security Engineer – Design and deploy security solutions including firewalls, IDS/IPS, and endpoint protection across enterprise systems.
Information Security Engineer – Design and deploy security solutions including firewalls, IDS/IPS, and endpoint protection across enterprise systems..ffb97545.png&w=16&q=75&dpl=dpl_6TSu5AqX4Gsythkwbfan4SsZGFHu) Threat Intelligence Analyst – Analyze threat patterns, monitor attack vectors, and provide actionable intelligence to mitigate risks.
Threat Intelligence Analyst – Analyze threat patterns, monitor attack vectors, and provide actionable intelligence to mitigate risks..ffb97545.png&w=16&q=75&dpl=dpl_6TSu5AqX4Gsythkwbfan4SsZGFHu) Incident Response Engineer – Lead the investigation and remediation of security breaches, minimizing damage and recovery time.
Incident Response Engineer – Lead the investigation and remediation of security breaches, minimizing damage and recovery time..ffb97545.png&w=16&q=75&dpl=dpl_6TSu5AqX4Gsythkwbfan4SsZGFHu) Vulnerability Management Specialist – Perform security assessments, penetration testing, and patch management to reduce exposure to attacks.
Vulnerability Management Specialist – Perform security assessments, penetration testing, and patch management to reduce exposure to attacks..ffb97545.png&w=16&q=75&dpl=dpl_6TSu5AqX4Gsythkwbfan4SsZGFHu) Cloud Security Consultant – Advise organizations on best practices for securing multi-cloud deployments, identity management, and compliance frameworks.
Cloud Security Consultant – Advise organizations on best practices for securing multi-cloud deployments, identity management, and compliance frameworks.
Featured in

for successfully completing the 'Cybersecurity Job Program' course conducted from 12 Aug 2025 to 27 Jan 2026
Add a Industry Recognized
Certificate To Your Resume
Industry Recognized
Certificate
Learn the best from the best

Career Advancements
Elevate your career with a respected certificate

Industry Respect
Gain credibility in the field

Networking
Connect with experts and peers

Opportunities
Attract exciting job prospects and promotions


for successfully completing the 'Cybersecurity Job Program' course conducted from 12 Aug 2025 to 27 Jan 2026

100% Moneyback Guarantee
Hear from our Learners












Looking for help? Here are our most frequently asked questions
What is a Job Program?
A Job Program is a rigorous, outcome-driven training designed to help you transition into a targeted role through live classes, 1:1 Customized projects, 1:1 mentorship and job-readiness support. You will get access to dedicated placement manager.
Who should enroll in this Job Program?
Professionals aiming for role transition, career acceleration or re-starting their careers—including early-career engineers and working professionals wanting to switch domains.
What will I get apart from live classes?
You get hands-on projects, structured assignments, doubt support, interview preparation, and a clear learning roadmap aligned to the job role. 1:1 Mentor for Project building & Certification, 1:1 Interview Preparation Support, 1:1 Placement Manager, 1:1 Profile Building
What is the weekly time commitment?
Typically 6–10 hours per week including live sessions and guided self-work. The program is designed to be manageable with a full-time job.
Will I get placement assistance?
You receive end‑to‑end job readiness support—resume/LinkedIn review, mock interviews, portfolio guidance and job opportunities.
Do I need prior experience?
Basic programming/technical familiarity helps, but the program includes foundations and bridges skill gaps with guided practice.

What is a Job Program?
A Job Program is a rigorous, outcome-driven training designed to help you transition into a targeted role through live classes, 1:1 Customized projects, 1:1 mentorship and job-readiness support. You will get access to dedicated placement manager.

Who should enroll in this Job Program?
Professionals aiming for role transition, career acceleration or re-starting their careers—including early-career engineers and working professionals wanting to switch domains.

What will I get apart from live classes?
You get hands-on projects, structured assignments, doubt support, interview preparation, and a clear learning roadmap aligned to the job role. 1:1 Mentor for Project building & Certification, 1:1 Interview Preparation Support, 1:1 Placement Manager, 1:1 Profile Building

What is the weekly time commitment?
Typically 6–10 hours per week including live sessions and guided self-work. The program is designed to be manageable with a full-time job.

Will I get placement assistance?
You receive end‑to‑end job readiness support—resume/LinkedIn review, mock interviews, portfolio guidance and job opportunities.

Do I need prior experience?
Basic programming/technical familiarity helps, but the program includes foundations and bridges skill gaps with guided practice.
General FAQs
Everything you need to know












